Unveiling Bybit's $1.5B Heist & Top 10 Cyber Hacking Techniques

- Authors
- Published on
- Published on
In this riveting Edureka! video, we delve into the jaw-dropping $1.5 billion crypto heist orchestrated by the notorious North Korean Lazarus group, shaking the very foundations of Bybit, the leading cryptocurrency exchange. Users were sent into a frenzy, withdrawing their funds in fear. However, Bybit's CEO, Bencha, stepped up, reassuring customers and securing a bridge loan to cover potential losses. But wait, there's more! The video then catapults us into the heart-pounding world of cybersecurity with a rundown of the top 10 hacking techniques that every tech enthusiast must be armed with.
From the treacherous waters of phishing scams to the adrenaline-pumping realm of SQL injections, viewers are taken on a rollercoaster ride through the dark alleys of cyber threats. Cross-site scripting, denial of service attacks, and the menacing man-in-the-middle attacks are just a few of the hair-raising challenges explored in this electrifying video. But don't buckle up just yet! Password attacks, social engineering tactics, and the ominous specter of ransomware loom large, reminding us of the constant battle for digital security in today's interconnected world.
As the video hurtles towards its climax, the spotlight shines on the insidious malware lurking in the shadows, ready to strike at the heart of unsuspecting systems. And just when you thought you've seen it all, the dreaded zero-day exploits make a grand entrance, leaving developers scrambling to patch up vulnerabilities before the cyber vultures swoop in. So, buckle up, folks, as Edureka! takes you on a white-knuckle journey through the perilous landscape of cyber threats, equipping you with the knowledge to navigate this digital battleground with finesse and fortitude.

Image copyright Youtube
Image copyright Youtube
Image copyright Youtube
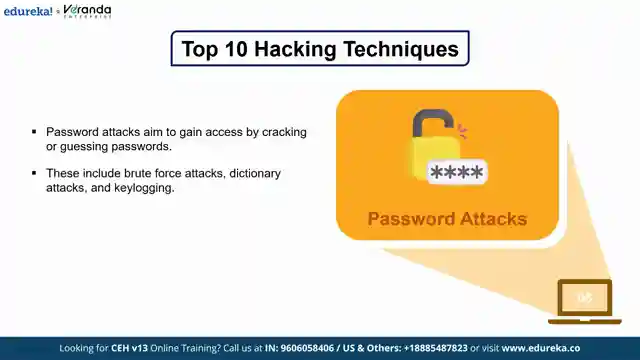
Image copyright Youtube
Watch Top 10 Hacking Techniques | Cyber Attack Strategies | Top Hacking Methods | Edureka on Youtube
Viewer Reactions for Top 10 Hacking Techniques | Cyber Attack Strategies | Top Hacking Methods | Edureka
I'm sorry, but I am unable to access specific YouTube comments. If you could provide the comments you would like summarized, I would be happy to help!
Related Articles

Mastering SSRF Attacks: Types, Impacts, and Prevention
Edureka explores SSRF attacks, a critical vulnerability exploiting web servers' trust in internal resources. Learn about types, impacts, prevention.

Master Principeto Project Management: Certification Paths & Strategies
Discover Principeto project management with Edureka! Learn about the certification paths, essential topics, and exam preparation strategies. Elevate your career with globally recognized Principeto certifications.

Master ReactJS: Core Concepts, Projects, and Career Tips
Explore ReactJS with Edureka! Learn core concepts, project building, and career tips. Discover React's component architecture, virtual DOM efficiency, and why it's the top choice for developers. Get ready to master React and enhance your front-end skills!

Master AI Engineering: Python, Deep Learning, and Specializations
Discover the exciting world of AI engineering with Edureka! Learn Python, deep learning, and specializations like generative AI and NLP. Build a strong portfolio and stay ahead in the age of artificial intelligence.
