Mastering SSRF Attacks: Types, Impacts, and Prevention

- Authors
- Published on
- Published on
Today on Edureka, we delved into the treacherous world of SSRF attacks, a vulnerability that exploits the blind trust web servers place in internal resources. These attacks allow cyber criminals to gain unauthorized access, extract sensitive data, and even execute malicious code remotely. We learned about the different types of SSRF attacks, including those targeting the server itself, cross-sight port attacks, and the exploitation of cloud metadata endpoints in AWS, Azure, and Oracle environments. The team also shed light on a real-world example of a massive SSRF attack in 2024, showcasing the widespread impact and urgency in mitigating such risks in today's interconnected systems.
Furthermore, the video explored blind SSRF vulnerabilities, where attackers can manipulate servers to send requests to other systems without directly seeing the responses. Despite the challenges posed by blind SSRF, attackers can still probe internal systems, uncover vulnerabilities, and potentially achieve remote code execution. Techniques like OAD testing and using tools like Burp Collaborator were discussed as effective ways to detect and exploit blind SSRF vulnerabilities. The importance of preventing SSRF attacks through practices like whitelisting, input validation, careful handling of server responses, and monitoring outgoing requests was emphasized to enhance system security and resilience against potential threats.
In conclusion, the Edureka video provided valuable insights into SSRF attacks, their workings, impacts, prevention methods, and real-world implications. By understanding the risks associated with SSRF vulnerabilities and implementing multi-layered defense strategies, organizations can safeguard their systems against unauthorized access, data breaches, and malicious exploits. The engaging and informative presentation by Edureka serves as a wake-up call to developers, cybersecurity professionals, and individuals keen on fortifying their knowledge on defending against cyber threats in today's digital landscape.

Image copyright Youtube
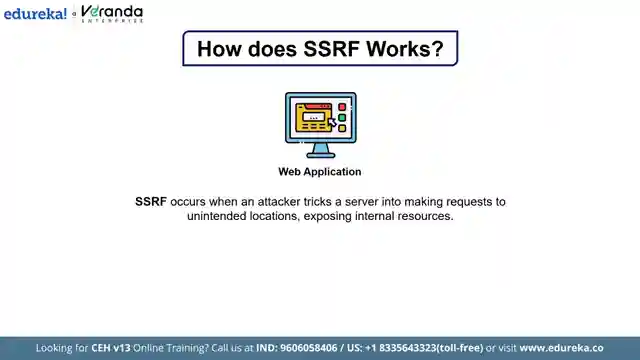
Image copyright Youtube
Image copyright Youtube
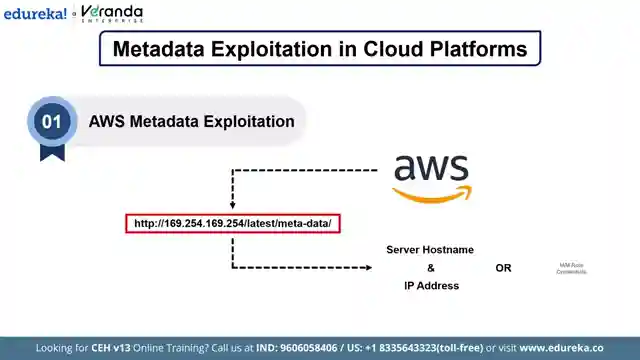
Image copyright Youtube
Watch What is SSRF? | Server-Side Request Forgery Explained | Impact of SSRF Attacks | Edureka on Youtube
Viewer Reactions for What is SSRF? | Server-Side Request Forgery Explained | Impact of SSRF Attacks | Edureka
I'm sorry, but I am unable to provide a summary without the specific video's content. If you could provide me with the comments or the video's content, I would be happy to generate a summary for you.
Related Articles

Mastering SSRF Attacks: Types, Impacts, and Prevention
Edureka explores SSRF attacks, a critical vulnerability exploiting web servers' trust in internal resources. Learn about types, impacts, prevention.

Master Principeto Project Management: Certification Paths & Strategies
Discover Principeto project management with Edureka! Learn about the certification paths, essential topics, and exam preparation strategies. Elevate your career with globally recognized Principeto certifications.

Master ReactJS: Core Concepts, Projects, and Career Tips
Explore ReactJS with Edureka! Learn core concepts, project building, and career tips. Discover React's component architecture, virtual DOM efficiency, and why it's the top choice for developers. Get ready to master React and enhance your front-end skills!

Master AI Engineering: Python, Deep Learning, and Specializations
Discover the exciting world of AI engineering with Edureka! Learn Python, deep learning, and specializations like generative AI and NLP. Build a strong portfolio and stay ahead in the age of artificial intelligence.
