Mastering Secrets Management in IT: IBM Technology Insights

- Authors
- Published on
- Published on
In this riveting video from IBM Technology, the team delves into the clandestine world of secrets management within the realm of IT. They tackle the age-old question of how to safeguard sensitive information like passwords, API keys, and cryptographic keys from prying eyes. The discussion revolves around the challenges of storing these secrets securely, highlighting issues such as sprawl, clear storage, and the critical need for access control.
To combat these challenges, the experts propose a centralized approach to secrets management, advocating for encryption of clear information, implementation of access control measures, continuous monitoring of access, and regular rotation of secrets to enhance security. They emphasize the importance of authentication, authorization, administration, and monitoring in a robust secrets management system, along with the ability to create, read, update, and delete secrets as needed.
The architectural layout of such a system is explored, with users, applications, and cloud instances attempting to access encrypted secrets stored in a secure data repository. The secrets management system acts as a gatekeeper, ensuring only authorized entities can access the sensitive information while also facilitating the dynamic generation of unique, time-based secrets for added protection. The experts stress the complexity of building such a system from scratch and recommend leveraging enterprise-class secrets management tools for a more efficient and secure approach.

Image copyright Youtube

Image copyright Youtube

Image copyright Youtube
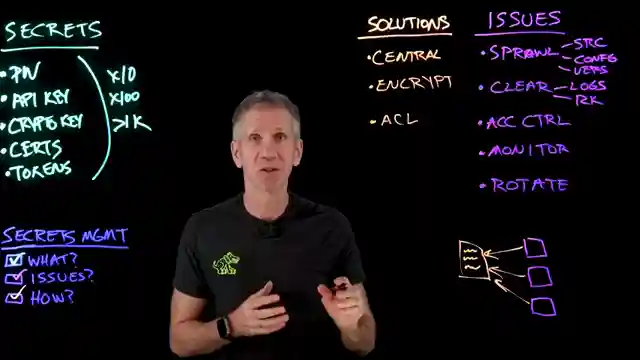
Image copyright Youtube
Watch Secrets Management: Secure Credentials & Avoid Data Leaks on Youtube
Viewer Reactions for Secrets Management: Secure Credentials & Avoid Data Leaks
Discussion about the game Uno
Comparisons between Uno and other card games
Suggestions for different variations of Uno
Memories of playing Uno with friends and family
Strategies for winning Uno games
Jokes and memes related to Uno
Requests for a tutorial on how to play Uno
Sharing personal experiences with Uno
Debates on the best house rules for Uno
Questions about where to buy Uno decks
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
