Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data

- Authors
- Published on
- Published on
In this riveting episode by IBM Technology, we delve into the thrilling world of data utilization in enterprises. Over the past decade, data has become more than just numbers on a screen - it's a powerhouse driving business intelligence and AI advancements. The team explores the fusion of data from various enterprise sources to extract valuable insights and train cutting-edge AI models like Gen AI and RAG. But with great data comes great responsibility - the challenge lies in safeguarding this amalgamated data against unauthorized access.
To tackle this challenge head-on, the team devises ingenious strategies to protect the sanctity of merged data. From traditional access controls to treating data warehouses as distinct assets, they leave no stone unturned in fortifying the data fortress. Data virtualization emerges as a game-changer, offering a dynamic runtime control mechanism tailored to user access rights. By creating virtualized outputs specific to user permissions, the team ensures a secure and efficient data access environment.
Moreover, the concept of filtering query results and implementing birthright access based on user roles injects a new level of sophistication into data protection strategies. Birthright access streamlines data access based on user identity and role, simplifying the process and enhancing security measures. And let's not forget the crucial aspect of compliance - ensuring all actions are observable and monitored closely to maintain data integrity. With these innovative strategies in their arsenal, the team at IBM Technology is at the forefront of safeguarding merged data in the dynamic landscape of enterprise data utilization.

Image copyright Youtube

Image copyright Youtube
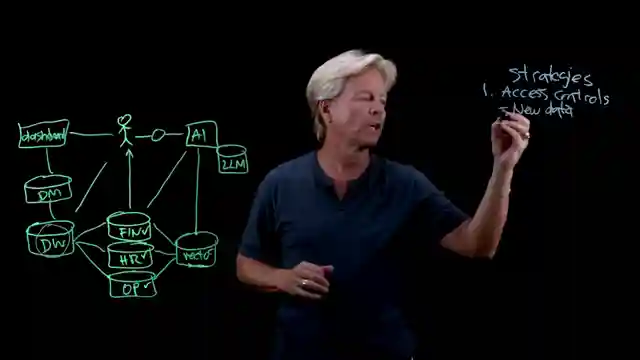
Image copyright Youtube
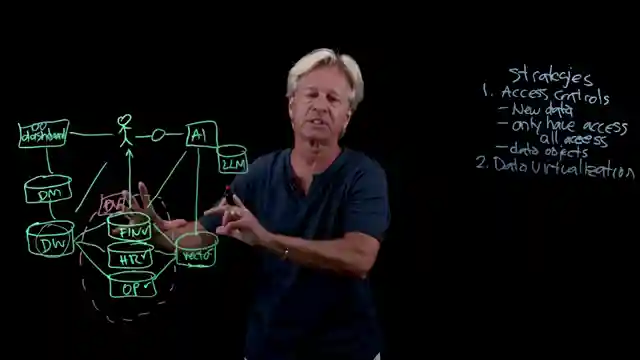
Image copyright Youtube
Watch Protecting Merged Data: Strategies for Governance & Access Control on Youtube
Viewer Reactions for Protecting Merged Data: Strategies for Governance & Access Control
Interest in learning more about Data Virtualization implementation
Greeting to IBM
Concerns about stealing public data for profit
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
