Mastering Phishing Defense: Techniques, Red Flags, and Protection

- Authors
- Published on
- Published on
Today on Edureka, we delve into the treacherous world of phishing attacks, a cunning cyber threat that preys on human vulnerability. These attacks, masquerading as trusted sources, aim to deceive individuals into divulging sensitive information like passwords and financial details. From bulk email phishing to spear phishing targeting specific individuals like CEOs, these tactics are as dangerous as they are effective. The nefarious business email compromise (BEC) scheme, where hackers hijack legitimate accounts to send fake invoices, is a costly example of the havoc phishing can wreak.
But the deception doesn't stop at emails; SMS phishing (smishing) and voice phishing (vishing) are on the rise, with scammers using text messages and phone calls to lure victims into sharing confidential data. Social media platforms have also become hunting grounds for hackers, tricking users into compromising their accounts through clever ruses. Identifying a phishing attempt is crucial, with red flags including urgent demands, requests for sensitive data, poor grammar, generic greetings, and fake URLs. By staying vigilant and recognizing these signs, individuals can thwart phishing attacks before they strike.
To shield oneself against these cyber predators, implementing multi-factor authentication and verifying sources before clicking on links are vital precautions. Education is key, with organizations urged to provide security awareness training to help staff detect phishing attempts. Utilizing security tools such as anti-phishing filters and spam blockers can fortify defenses against malicious emails. Reporting suspicious messages to the relevant authorities or IT departments is crucial in combating phishing attacks. By raising awareness and adopting proactive measures, individuals can fortify their cyber defenses and safeguard their valuable data from evolving phishing threats.

Image copyright Youtube

Image copyright Youtube
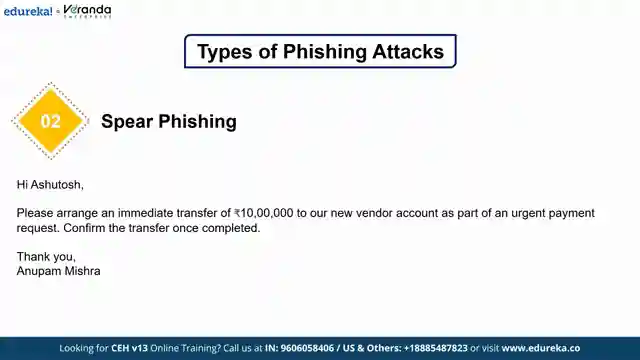
Image copyright Youtube
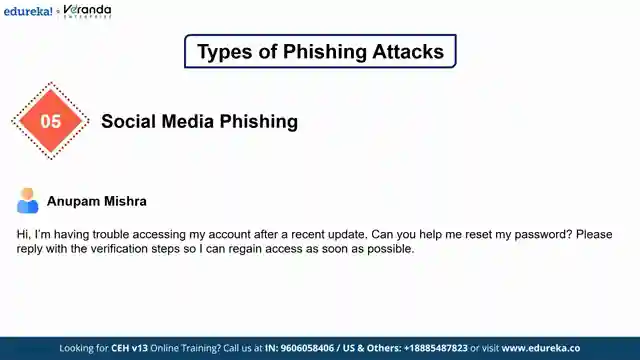
Image copyright Youtube
Watch Phishing Attacks Explained | How to Prevent Phishing Attacks | Phishing Attack Examples | Edureka on Youtube
Viewer Reactions for Phishing Attacks Explained | How to Prevent Phishing Attacks | Phishing Attack Examples | Edureka
Informative content
Positive feedback on the information provided
Related Articles

Mastering SSRF Attacks: Types, Impacts, and Prevention
Edureka explores SSRF attacks, a critical vulnerability exploiting web servers' trust in internal resources. Learn about types, impacts, prevention.

Master Principeto Project Management: Certification Paths & Strategies
Discover Principeto project management with Edureka! Learn about the certification paths, essential topics, and exam preparation strategies. Elevate your career with globally recognized Principeto certifications.

Master ReactJS: Core Concepts, Projects, and Career Tips
Explore ReactJS with Edureka! Learn core concepts, project building, and career tips. Discover React's component architecture, virtual DOM efficiency, and why it's the top choice for developers. Get ready to master React and enhance your front-end skills!

Master AI Engineering: Python, Deep Learning, and Specializations
Discover the exciting world of AI engineering with Edureka! Learn Python, deep learning, and specializations like generative AI and NLP. Build a strong portfolio and stay ahead in the age of artificial intelligence.
