Mastering Gen AI Tech: Preventing LLMjacking Attacks

- Authors
- Published on
- Published on
In the latest episode from IBM Technology, we delve into the fascinating world of Gen AI, a groundbreaking technology that's changing the game in computing faster than a Bugatti on the Autobahn. This marvel can decipher your words using natural language processing and whip up a whole new document with just a simple prompt. But hold on to your helmets because running this cutting-edge tech can drain your bank account faster than a Formula 1 pit stop. Yes, someone's gotta foot the bill, and you might unknowingly be the one left holding the bag for a joyride you didn't even take.
Enter the villain of our story: LLMjacking. A dastardly scheme where cyber-crooks sneak into your cloud instance like a thief in the night, hijacking your resources and leaving you with a bill that could make a sheikh blush. These nefarious individuals exploit vulnerabilities in your cloud security, possibly using stolen credentials like a master key to your digital kingdom. Imagine finding out that your cloud instance has been transformed into a playground for these cyber bandits, running their own large language models at your expense.
To combat this digital highway robbery, our heroes at IBM Technology lay out a roadmap to fortify your defenses against such treacherous attacks. From safeguarding your credentials like precious jewels in a vault to ferreting out shadow AI lurking in the shadows of your system, every step is crucial in this high-stakes game of cyber chess. Utilizing tools for vulnerability management, patching software, and scrutinizing cloud configurations, you can turn the tables on these cyber marauders and protect your digital domain from becoming a den of thieves. So rev up your engines, tighten your grip on the wheel, and follow these expert tips to steer clear of the perils of LLMjacking in the fast lane of the digital world.

Image copyright Youtube

Image copyright Youtube

Image copyright Youtube
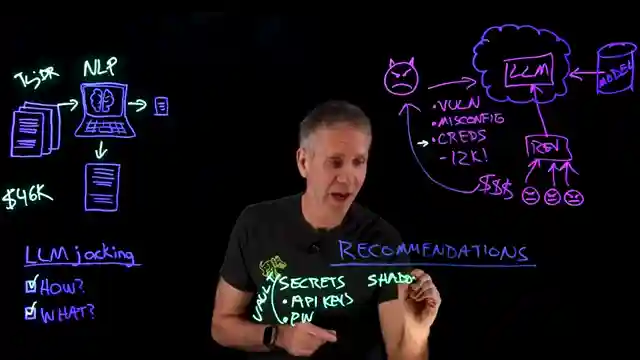
Image copyright Youtube
Watch What is LLMJacking? The Hidden Cloud Security Threat of AI Models on Youtube
Viewer Reactions for What is LLMJacking? The Hidden Cloud Security Threat of AI Models
Positive feedback on the whiteboard style used in the video
Appreciation for the session on understanding risk surface and mitigation
Surprise at learning about a problem they didn't know could happen
Gratitude for the content provided
Thankful for the useful information shared
Comment on finally understanding the topic after watching the video
Expression of surprise
Confusion or contemplation emoji used at the end of the comment
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
