Mastering DDoS Attacks: Types, Tools, and Simulations

- Authors
- Published on
- Published on
Today on Edureka!, we delve into the treacherous world of cyber warfare, focusing on the infamous DDoS attacks that wreak havoc on unsuspecting servers. These attacks, like a relentless swarm of angry wasps, flood the targeted systems with malicious traffic, causing chaos and rendering them inaccessible. The transcript vividly describes the different types of DDoS attacks, from the brute force of volumetric assaults to the cunning protocol and application layer infiltrations that cripple servers from within.
The narrative takes a dramatic turn as it recounts the catastrophic 2016 Mai botnet attack, a digital onslaught of unprecedented scale that brought internet giants like Twitter, Netflix, and Reddit crashing down. The sheer magnitude of 1.2 terabytes per second of malicious traffic unleashed during this cyber siege serves as a chilling reminder of the destructive power wielded by cyber criminals. The financial repercussions, loss of customer trust, and potential security breaches resulting from such attacks loom like dark clouds over the digital landscape.
The transcript then shifts its focus to the arsenal of tools employed by hackers in their nefarious pursuits, from the rudimentary yet effective LOIC and HOIC to the stealthy Slowloris and the cunning R-U-Dead-Yet. Each tool is a digital weapon designed to exploit vulnerabilities in server defenses, launching relentless attacks that overwhelm and incapacitate even the most robust systems. The demonstration of a DDoS attack using virtual machines, with Kali Linux as the attacker and Ubuntu as the victim, provides a chilling simulation of the havoc these tools can wreak in the wrong hands.
As the smoke clears and the dust settles, the video concludes with a call to action, urging viewers to arm themselves with knowledge and vigilance in the face of cyber threats. Like a rallying cry on the battlefield, Edureka! encourages its audience to stay informed, engage with the channel, and fortify their defenses against the ever-present danger of cyber attacks. In this digital age where anonymity is both shield and sword, the battle for cybersecurity rages on, and only those armed with awareness and preparedness can hope to emerge victorious.

Image copyright Youtube
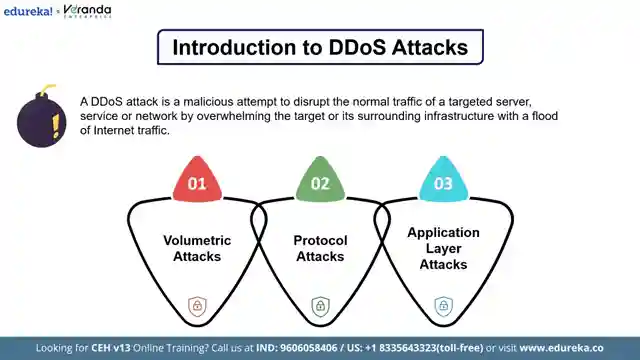
Image copyright Youtube
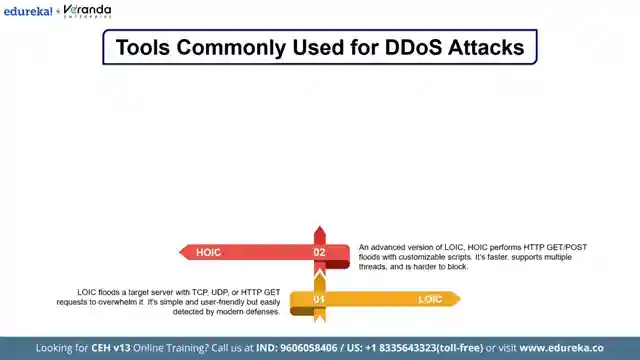
Image copyright Youtube
Image copyright Youtube
Watch DDoS Attack | What is a DDoS Attack? | DDoS Attack Explained | Edureka on Youtube
Viewer Reactions for DDoS Attack | What is a DDoS Attack? | DDoS Attack Explained | Edureka
Summary: The video seems to have sparked a lot of discussion among viewers, with a variety of opinions and reactions being shared in the comments section.
Top ten commented topics:
The quality of the content
Comparisons to other similar videos
Critiques of the presenter's style
Questions about the topic being discussed
Personal anecdotes related to the content
Requests for future video topics
Debates among viewers about specific points made in the video
Compliments on the production value
Recommendations for other channels or resources
Jokes and humor related to the video's content
Related Articles

Mastering SSRF Attacks: Types, Impacts, and Prevention
Edureka explores SSRF attacks, a critical vulnerability exploiting web servers' trust in internal resources. Learn about types, impacts, prevention.

Master Principeto Project Management: Certification Paths & Strategies
Discover Principeto project management with Edureka! Learn about the certification paths, essential topics, and exam preparation strategies. Elevate your career with globally recognized Principeto certifications.

Master ReactJS: Core Concepts, Projects, and Career Tips
Explore ReactJS with Edureka! Learn core concepts, project building, and career tips. Discover React's component architecture, virtual DOM efficiency, and why it's the top choice for developers. Get ready to master React and enhance your front-end skills!

Master AI Engineering: Python, Deep Learning, and Specializations
Discover the exciting world of AI engineering with Edureka! Learn Python, deep learning, and specializations like generative AI and NLP. Build a strong portfolio and stay ahead in the age of artificial intelligence.
