Mastering Cybersecurity Essentials: CIA, PDR, PPT, and 24/7 Vigilance

- Authors
- Published on
- Published on
In this riveting video from IBM Technology, the enigmatic world of cybersecurity is laid bare, revealing its intricate web of challenges and adversaries. The team embarks on a quest to demystify this digital battlefield, distilling the essence of cybersecurity down to its core principles. Enter the CIA triad – not the spy agency, mind you, but a trio of pillars: confidentiality, integrity, and availability. These are the holy grails that defenders must safeguard to thwart the nefarious schemes of cyber villains.
But how does one navigate this treacherous terrain, you may wonder? Fear not, for the team introduces the PDR mantra: prevention, detection, and response. It's a symphony of strategies and technologies working in harmony to fortify the digital ramparts. From the impenetrable fortresses of cryptography to the vigilant watchtowers of SIEM systems, every tool plays a crucial role in the cybersecurity arsenal. And when all else fails, the valiant defenders must rally for a swift and decisive response, guided by the battle cry of SOAR – security, orchestration, automation, and response.
Yet, in this saga of bits and bytes, one must not overlook the human element. People, processes, and technology form a trinity that must collaborate seamlessly to uphold the cybersecurity stronghold. It's not just about fancy gadgets and gizmos; it's about the skilled hands and sharp minds that wield them. Training, expertise, and sound decision-making are the unsung heroes in this digital epic. As the team underscores, the true victory lies in the harmonious integration of these three elements, ensuring a robust defense against the relentless onslaught of cyber threats.
And when should one remain vigilant in this ever-evolving landscape of cybersecurity? The answer, dear viewers, is simple yet profound: all the time. In a world where the adversaries never sleep, where a single misstep could spell disaster, the defenders must stand guard 24/7. It's a perpetual dance of wits and wills, where complacency is the deadliest foe. So, as the sun sets on this enlightening journey through the realm of cybersecurity, remember this: the battle rages on, and only the vigilant shall emerge victorious in this digital crusade.

Image copyright Youtube

Image copyright Youtube
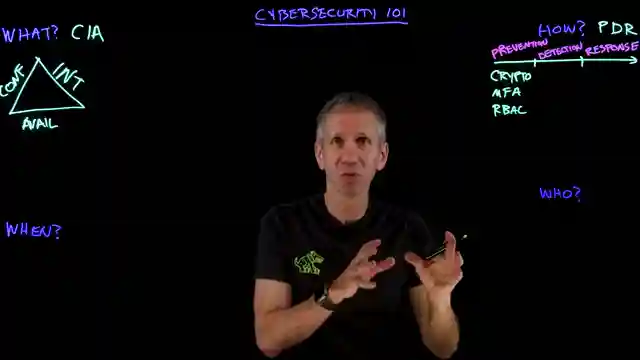
Image copyright Youtube

Image copyright Youtube
Watch Cybersecurity Explained in 3 Acronyms: CIA, PDR, & PPT on Youtube
Viewer Reactions for Cybersecurity Explained in 3 Acronyms: CIA, PDR, & PPT
Comment about the importance of PDR (Prevention, Detection, Response)
Mention of the US government's involvement in professional development using PowerPoint
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
