Demystifying Cyber Kill Chain: Stages, Evolution, and Role in Cybersecurity

- Authors
- Published on
- Published on
Today, we're diving into the riveting world of cyber security with edureka! as our guide. They're taking us on a thrilling journey through the Cyber kill chain, a model that dissects how cyber attackers operate and how we can thwart their nefarious plans. This model, adapted from the military, is a step-by-step framework that helps organizations identify and halt cyber attacks at different stages. It's like a strategic battle plan in the digital realm, arming us with the knowledge to outsmart the cyber baddies at every turn.
We're breaking down the seven stages of the Cyber kill chain, each playing a crucial role in an attack. From reconnaissance, where attackers gather intel on their targets, to actions on objectives, where they achieve their malicious goals, every step is a piece of the puzzle. But wait, there's more! We're also comparing the Cyber kill chain to the miter attack framework, exploring how these two heavyweights stack up in the cyber security arena. While the Cyber kill chain offers a high-level overview, miter attack delves into the nitty-gritty details of attack execution, giving us a comprehensive view of the cyber battlefield.
As cyber threats evolve and grow more sophisticated, the Cyber kill chain has had to adapt to stay ahead of the game. Attackers are now employing advanced techniques like fileless malware and AI-driven attacks, challenging defenders to up their game. Despite its strengths, the Cyber kill chain isn't without its weaknesses. It focuses heavily on malware and follows a rigid structure that doesn't always fit the bill for modern threats. To overcome these limitations, organizations are urged to complement the Cyber kill chain with other frameworks and advanced technologies, creating a more robust defense against cyber threats.
Image copyright Youtube

Image copyright Youtube
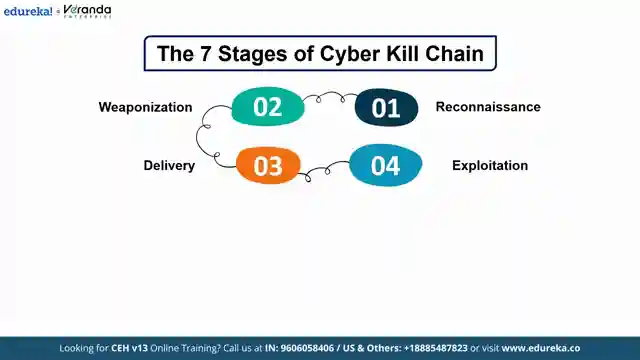
Image copyright Youtube
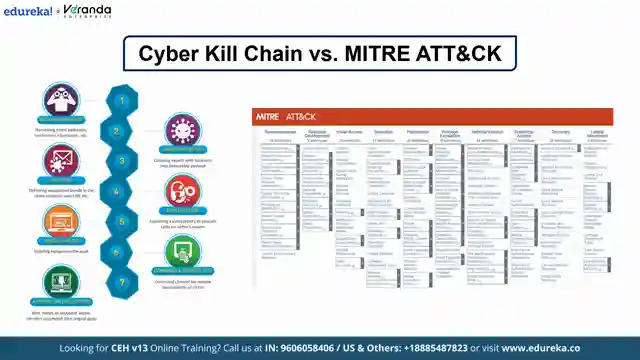
Image copyright Youtube
Watch Cyber Kill Chain | What is Cyber Kill Chain? | The Seven Stages of a Cyberattack | Edureka on Youtube
Viewer Reactions for Cyber Kill Chain | What is Cyber Kill Chain? | The Seven Stages of a Cyberattack | Edureka
Unfortunately, I cannot provide a summary without the specific video content. If you could provide more details or a specific video for reference, I would be happy to help summarize the comments for you.
Related Articles

Mastering SSRF Attacks: Types, Impacts, and Prevention
Edureka explores SSRF attacks, a critical vulnerability exploiting web servers' trust in internal resources. Learn about types, impacts, prevention.

Master Principeto Project Management: Certification Paths & Strategies
Discover Principeto project management with Edureka! Learn about the certification paths, essential topics, and exam preparation strategies. Elevate your career with globally recognized Principeto certifications.

Master ReactJS: Core Concepts, Projects, and Career Tips
Explore ReactJS with Edureka! Learn core concepts, project building, and career tips. Discover React's component architecture, virtual DOM efficiency, and why it's the top choice for developers. Get ready to master React and enhance your front-end skills!

Master AI Engineering: Python, Deep Learning, and Specializations
Discover the exciting world of AI engineering with Edureka! Learn Python, deep learning, and specializations like generative AI and NLP. Build a strong portfolio and stay ahead in the age of artificial intelligence.
